How to collect and analyze Netmon logs Ideally, we capture the logs between client and servers in order to check issues from network point of perspective
Analyze Netmon logs
- Download Netmon from this link: https://www.microsoft.com/en-us/download/4865
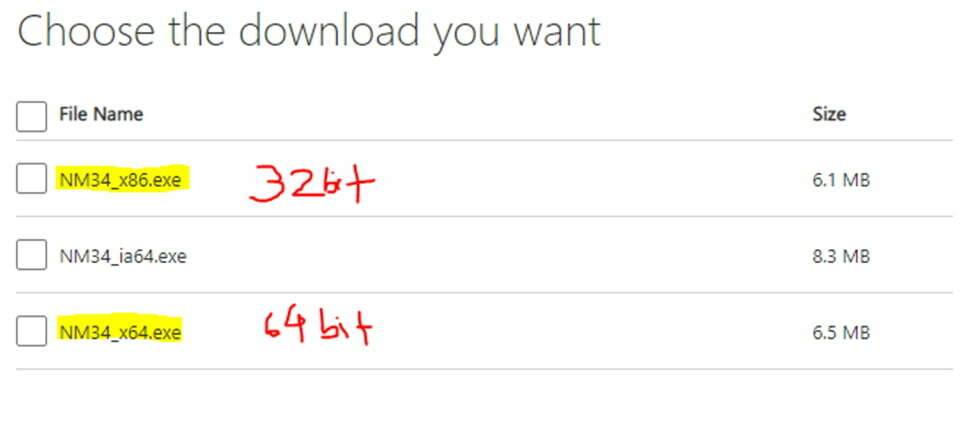
- Choose either 32 bit or 64 bit as per the machines configuration
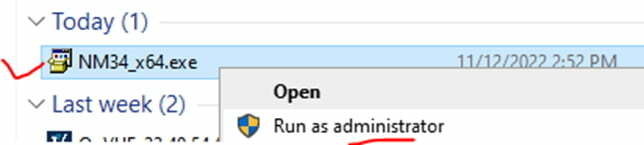
- Install executable
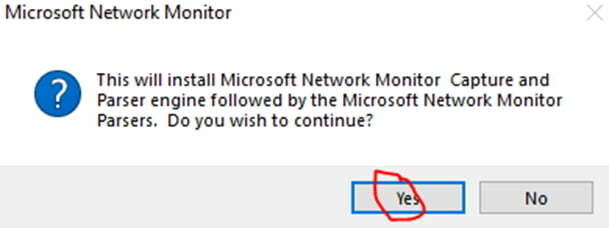
- Hit Next
- Install it and finish
Steps to capture Netmon logs:
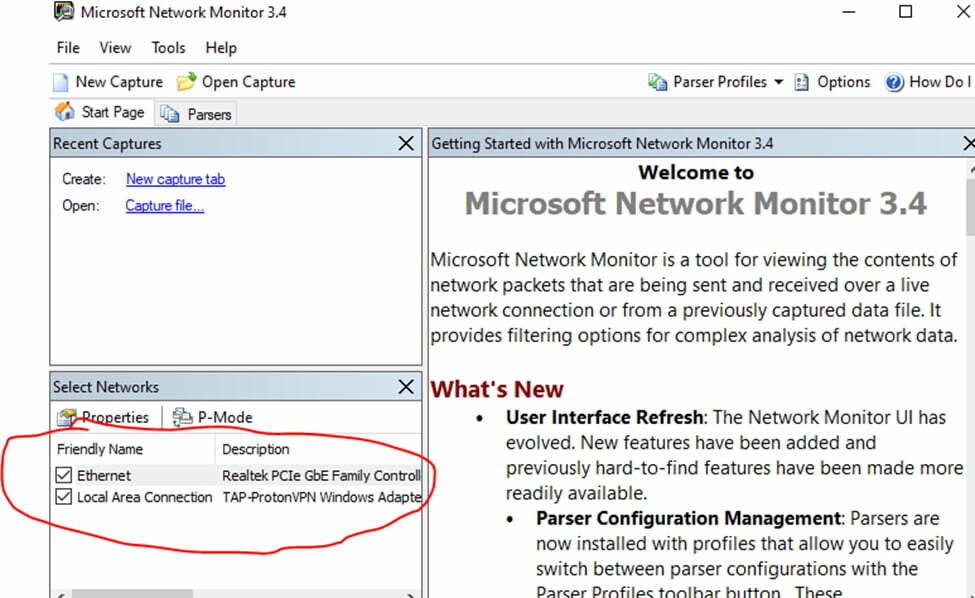
Open Netmon and run as admin so that it can detect all NIC cards of the machine and select all of them before capturing network logs
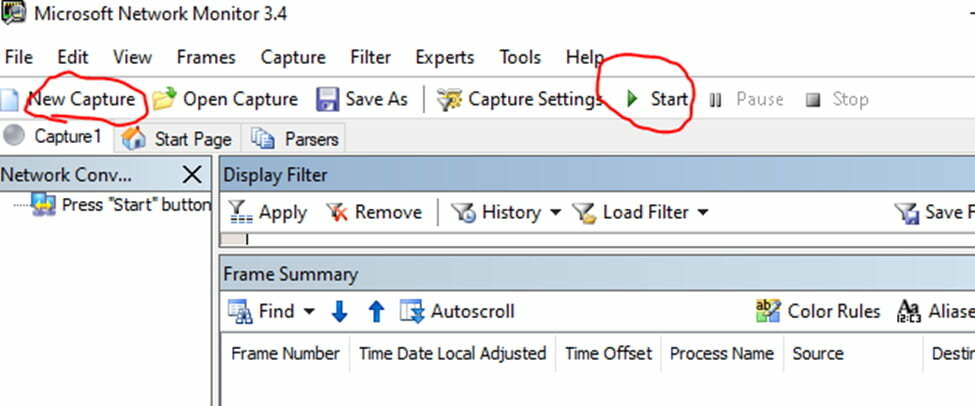
Post that click on new capture and hit start
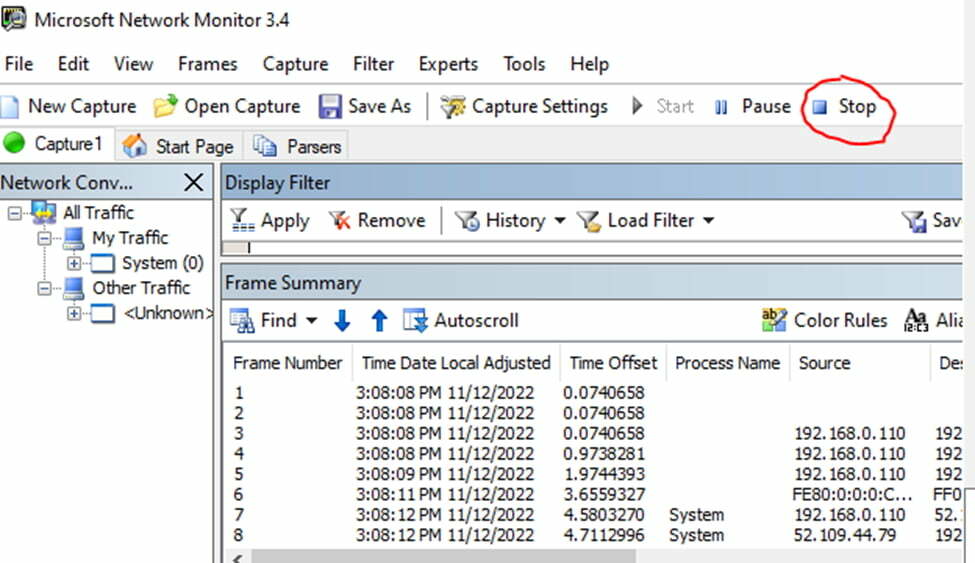
Repro the issue and make sure Netmon is running in the background, once issue is reproduced then stop the traces
Finally save the logs à file à save as à give a specific nameà clientnetmonlogs à Okay
Filters used for Netmon in order to read the logs
Below is the section where we have apply filters
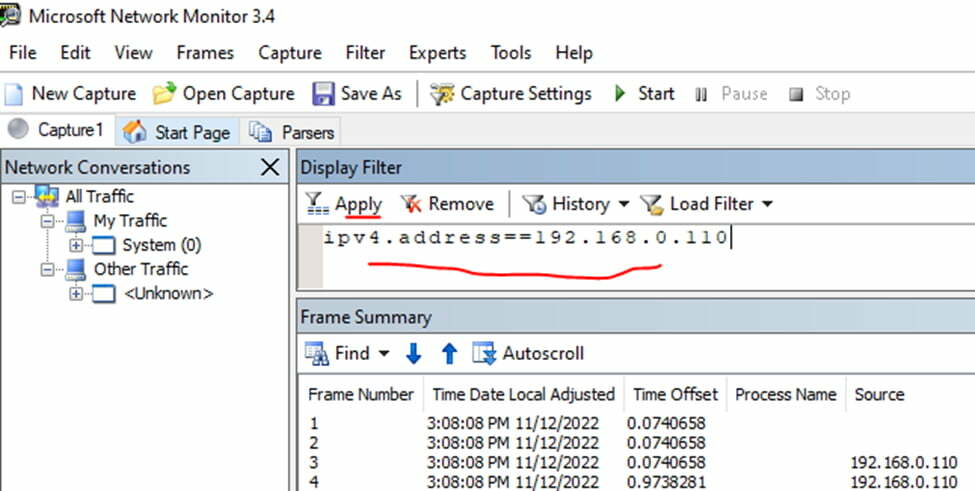
e.g.
- Ipv4.address==”client ip” and ipv4.address==”server ip”
- Tcp.port==
- Udp.port==
- Icmp
- Arp
- Property.tcpretranmits
- Property.tcprequestfastretransmits
- Tcp.flags.syn==1
- Tcp.flags.reset==1
- tcp.port==5061 // SIP over TLS. This is used by most functions of OCS
- && tcp.port==5060 // SIP over TCP
- && tcp.port==5062 // Default SIP for the A/V edge
- && tcp.port==5063 // Default SIP for the A/V Conferencing server
- && tcp.port==443 // HTTPS, TCP STUN
- && udp.port==3478 // UDP STUN
- && tcp.port==8057 // PSOM
- && tcp.port==135 // RPC endpoint mapper used on front end servers for WMI and DCOM
- && dns
Conclusion : Post reading above blog now I am confident on how to capture and read the netmon logs
Don’t forget to support us by following us on Google News or Returning to the home page TopicsTalk
Join Telegram and WhatsApp for More updates
Follow us on social media






